I do a lot of CLI demos when showing off PSO and K8s and Helm and all the cool things they can do. I made the switch to ZSH and oh my zsh and I really like using it for the past year.
After trying a few different themes and prompts I settled on the following using the “Agnoster” theme for oh-my-zsh. I added the kube-ps1 plugin so I can see what cluster I am using.

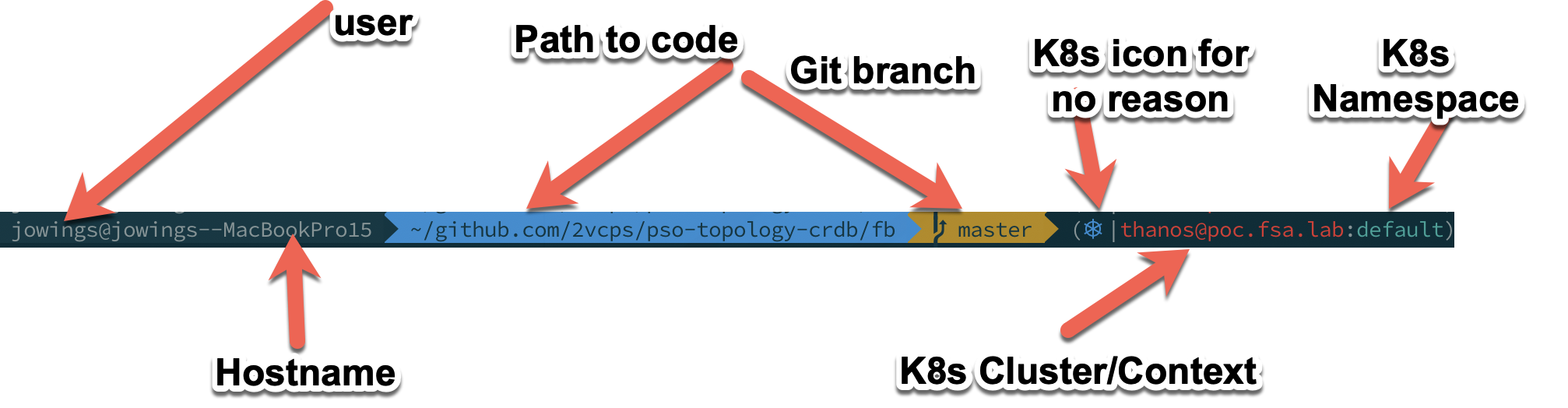
One annoyance is getting when I am in some github repo for a demo deploying containers and ingresses and stuff the prompt gets so long the wordwrap on iTerm window makes me crazy.

Break down of my full prompt

- User name – good to know, I have cloud instances that are ‘ubuntu’ or ‘ec2-user’ so this helps me know what I am working on.
- Hostname – I can shorten this, but there is a jamf policy on this machine that sets it back to this monstrosity. I mean, really who forces the username into the hostname?
- Path to code – Do I need to see this full path all the time? Probably not.
- Git Branch – Good to know when I am coding.
- K8s Icon – Non-negotiable. It is awesome.
- K8s Cluster/Context – I currently am testing 9 versions of K8s and different clusters. This keeps me sane.
- K8s Namespace – This for me is nearly always default since I use kubectl -n <namespace> to do things in namespaces.
I saw someone with a different shell with the cool shorthand path and I felt like that should be an option for my prompt. I like everything else about the agnoster theme. So how can I fix it.
First I found this plugin for ohmyzsh:
https://github.com/ohmyzsh/ohmyzsh/tree/master/plugins/shrink-path
So I enabled it within my .zshrc: below is my plugins and 2 important sections.
plugins=(
git
kube-ps1
vscode
kubectl
shrink-path
)
source $ZSH/oh-my-zsh.sh
PROMPT='$(kube_ps1)'$PROMPTThe extra “PROMPT” is to add the kubernetes information to the existing prompt generated by the above ‘source oh-my-zsh.sh’
This didn’t magically fix the prompt like I hoped. Somewhere we have to tell the theme how to build the prompt.
If we edit the ~/.oh-my-zsh/themes/agnoster.zsh-theme we actually see the function that builds the prompt.
## Main prompt
build_prompt() {
RETVAL=$?
prompt_status
prompt_virtualenv
prompt_aws
prompt_context
prompt_dir
prompt_git
prompt_bzr
prompt_hg
prompt_end
}
PROMPT='%{%f%b%k%}$(build_prompt) 'Of course it is a function that calls a bunch of others and “prompt_dir” is the one we want to edit.
Change it from this:
prompt_dir() {
prompt_segment blue $CURRENT_FG '%~'
}To this:
prompt_dir() {
SHORT=$(shrink_path -f)
prompt_segment blue $CURRENT_FG $SHORT
}Now we are using “shrink_path -f” to shorten the directories in the path and storing it in the SHORT variable. Then displaying it in the same spot as full path was before.

Look at how that path was shortened! So far this is working for me on:
- Windows 10 WSL2 – Ubuntu 18.04
- Linux Server with Ubuntu 16.04 and 18.04
- Mac OSX Mojave